Healthcare IT and HIPAA Compliance: Choosing the Right Level Information Risk Management
October 8, 2020
Compliance with HIPAA and the growing list of privacy and security standards is essential to the growth of Healthcare IT companies. You know that you need to make HIPAA compliance and information risk management a high priority, but how do you choose the right level of risk management and compliance for your company? Determining the right approach requires a comprehensive understanding of your risks and the requirements of your customers and prospects. In this article, we will provide some basic considerations to help you determine your approach.
Understanding healthcare IT risk – why compliance isn’t enough
The rapid digital advancements across healthcare analytics, imaging, training, surgical equipment, wearable monitors (including FitBits and Smart Watches) and telehealth, have created an explosion in the volume of Electronic Protected Healthcare Information (ePHI) being generated, transmitted, processed and stored by payers, providers and business associates.
As the volume and footprint of ePHI have increased, so has the frequency and magnitude of cyber incidents. Breaches reported by the Office for Civil Rights (OCR) on their infamous “Wall of Shame“ indicate there were 350+ cases under investigation affecting over 12.6 million individuals at the close of Q3 2020. That represents a 30% increase over 2019.
Why are healthcare-related cyber incidents still increasing, even though HIPAA regulations have been in effect for 20 years? We think there are a few primary drivers; including:
- Choosing compliance over risk management – Healthcare businesses have treated HIPAA as a compliance requirement, and not a risk management protocol. More on that later.
- The deadly advance of cybercrime – The persistence and sophistication of cyber threat actors is continually increasing. In particular, healthcare settings are highly susceptible to ransomware that can impede their ability to deliver critical care. 2020 has seen the first instances of death related to ransomware, and many experts expect this will occur more frequently.
- The black market value of healthcare data – EMRs / ePHI often are the most valuable forms of PII for purposes of identity theft and fraud (e.g., fraudulent insurance claims.) Thus their value is far greater than other PII data sets, often selling for $250 to
Clearly, healthcare companies and Business Associates need to move beyond a compliance mindset to a risk management mindset and apply a practical approach that is right-sized for the unique needs of the business.
How do you choose a risk management and compliance strategy that works for YOU?
There is no one-size-fits-all solution for information risk management and HIPAA compliance. Choosing the right option depends largely on your business model, organizational goals, as well as factors like relative cost, the maturity of your business, and the requirements of your customers and prospects.
Here are the options to consider relative to cost, complexity, and customer requirements:
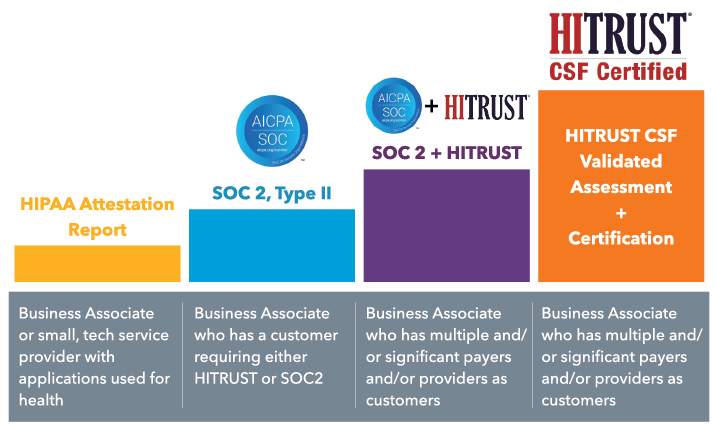
- HIPAA Attestation Reporting – is the easiest and most cost-effective assurance reporting to achieve. It is appropriate if your business is a startup or generic technology service provider that offers applications that can be used in healthcare and have minimal interaction with ePHI. Your business may have 1-2 customers requesting HIPAA compliance and/or HITRUST CSF or SOC 2 reporting.
- SOC 2, Type II – the next step up, SOC 2, Type II, applies is your company is classified as a true Business Associate and therefore needs to meet the “spirit and intention of HIPAA.” Given the potential synergies between SOC 2 and HITRUST CSF, SOC 2, Type II is often a good option for BAs that have a customer that will accept either a HITRUST CSF Validated Assessment or a SOC 2, Type II report.
- SOC 2 + HITRUST – should be considered by BAs that have multiple and significant payers and/or providers as customers. This reporting structure is applicable when a customer requests SOC 2 Type II reporting and evidence that you meet HITRUST requirements. SOC 2 + HITRUST is very robust in terms of security requirements; however, it can be simpler and more cost-effective to achieve than HITRUST Validated Assessment and Certification.
- Becoming HITRUST CSF Certified – HITRUST CFS certification may be required by larger healthcare plans and payor groups of their participating provider organizations. Therefore, if you are a BA that serves multiple and significant payers and/or providers such as hospitals and insurance companies, you may be required to be HITRUST CSF Certified.
Ensure that your compliance program is founded on risk management
There are two central tenets of HIPAA Security Rule that are virtually the same as any other security standard or framework:
- Risk analysis (Required): Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of the electronically protected health information held by the organization. Read HHS guidance on risk analysis requirements.
- Risk management: Implement security measures to reduce risk to reasonable and appropriate levels to ensure the confidentiality, availability and integrity of ePHI, protect against any reasonably anticipated threats or hazards to the security or integrity of ePHI, and protect against any reasonably anticipated uses or disclosures of EPHI that are not permitted or required under the HIPAA Privacy Rule.
These two core tenets of HIPAA are common to any relevant security standard or framework, including SOC 2 and HITRUST. The rationale is to ensure that each organization has an accurate understanding of cyber threats and risks to its business and can make informed decisions in applying risk management measures.
Unfortunately, these core tenets are often misunderstood and misapplied, especially by healthcare organizations – even when completing SOC 2 and/or HITRUST reporting.
Part of Aprio’s attestation services includes taking steps to empower our clients to effectively understand and apply these concepts to ensure that compliance requirements are addressed. More importantly, our teams stress the central reason for these concepts: protecting the business from cyber threats.
Aprio works closely with our clients to make sure the appropriate levels of privacy and security are achieved, so your healthcare IT organization can fulfill its central mission – to serve patients and other organizations that serve patients.
The bottom Line
Healthcare IT companies must face the fact that they are primary targets for cybercrime and must be proactive about their risk management and compliance reporting strategies. Although selecting the right compliance reporting option for your business is largely based on the customer requirements, simply pursuing compliance will not position the organization for growth and places the business, its customers and the health and safety of the public at risk.
If you need assistance with HIPAA compliance, data privacy and security risk management, contact Aprio to schedule a consultation.
Stay informed with Aprio.
Get industry news and leading insights delivered straight to your inbox.

