Not All SOC 2 Reports are Created Equal
December 6, 2019
Information security in and of itself is incredibly complex. And the framework for SOC 2 examination and reporting is equally complicated. So, it’s not surprising that often neither customer nor service organization understand the difference between a good SOC 2 report and a bad one. The quality and utility of SOC 2 is in the making of the report, not just the report itself.
If you’re in the market for SOC 2 reporting, ask yourself these questions:
- Does the SOC 2 audit firm understand information security and its importance to my business? Make sure the people who will service your business hold relevant professional certifications; e.g., CISA, CRISC, CISM, Security+, CIPP, CISSP, etc., and at the firm level ISO 27001 Certifying Body accreditation and PCI Qualified Security Assessors.
- Does the firm view themselves as a long-term cyber risk management business partner or a high-volume report production shop? Is their objective to maximize the effectiveness of your risk management and report quality – or to produce a report as quickly and easily as possible – to maximize their profit and report volume. Has the firm explained how the SOC 2 standard relates to your business, how it can be leveraged to strengthen your business’s cyber and privacy risk management, and how they can be a great partner to enable you to continuously improve your risk management posture?
- Has the firm provided a clear, common sense roadmap as to enable you to meet your risk management and assurance reporting objectives? Did they step me through the process; helping me to understand the requirements, identify gaps and provide guidance to ensure risk management and report quality meet our business needs?
A select few CPAs are experts in cyber security and compliance
SOC audit and reporting can only be performed by an independent CPA (Certified Public Accountant). However, not all CPAs are information security experts. Information security and risk management require highly specialized skills. To validate a provider’s information security expertise, look for firms that are ISO 27001 certifying bodies and/or PCI DSS QSA providers and whose personnel demonstrate commitment to continuing security expertise through security focused designations such as CISSP, CRISC, CISM, Security+ and PCI QSA.
In terms of technical depth and expertise, very few firms can match Aprio’s experience and expertise in cyber security and compliance; for example:
- Aprio’s SOC 2 personnel all have advanced degrees in and certifications in cyber security/privacy compliance and risk management,
- Aprio was one of the first CPA firms to achieve accreditation as an accredited ISO 27001 Certifying Body,
- Aprio was one of the first CPA firms to achieve accreditation as a PCI DSS QSA provider,
- Aprio’s Partner-in-Charge of Information Assurance, Dan Schroeder, CPA,CISM, CISA, CRISC, CIPT, PCI-QSA is the past chairperson of the AICPA Information Management Technology Assurance Committee and actually wrote and delivered the original SOC reporting training curriculum.
Download our SOC Provider Checklist for a complete list.
You can’t automate information risk management.
Automation and standardization can be a good thing but be weary of suppliers that boast of reports being done in volume. SOC 2 reports are not push-ups. Risk management by definition is a process that takes time and must be tailored to your particular business. If it was an off-the-shelf product, we would not have to worry about security. SOC 2 is highly valued for its flexibility and customizability. If a report is overly standardized and not specific, relevant and useful to your business, it won’t be useful to you or your customers.
Is my SOC provider’s business model based on generating high volume, standardized reports, or effective risk management consulting and reporting?
Equally as important as the business model and track record of your SOC 2 vendor, it’s crucial to understand whether the firm is philosophically aligned with you and invested in the long-term success of your information assurance program — or are they simply helping you check the box on SOC 2.
Look beyond the “sticker” to process and deliverables.
“Sticker syndrome” afflicts corporate leaders who believe that a SOC 2 report is the seal of approval that proves information security assurance — end of story. In fact, SOC 2 reporting is a means to an end, not the end in itself.
A shocking number of business leaders fail to meet their risk management responsibilities despite having — and asking for — all the right certifications and reports. Rather than passively accepting reports as a proxy for risk management, CIOs and other business leaders must approach risk management with an engaged and questioning mind, actively seeking out evidence that the business is doing the right things to protect against threats.
This journey begins with a thoughtful assessment of risks and potential risk response options, which leads to meaningful design of controls, ongoing monitoring and, finally, independent attestation in the form of a SOC 2 report.
What does a “good” SOC 2 report look like?
A SOC 2 report is supposed to (a) describe the service organization’s information assurance system, (b) describe the controls supporting the system, and (c) verify that controls are working properly. A good report is measured by its usability, relevance and
level of detail.
A “good” SOC 2 report makes it easy for users to:
- Ensure the service described is consistent with the service received.
- Understand the description of the system as it pertains to how the service is delivered and the design of security controls supporting the system.
- Understand the nature, timing and extent of tests.
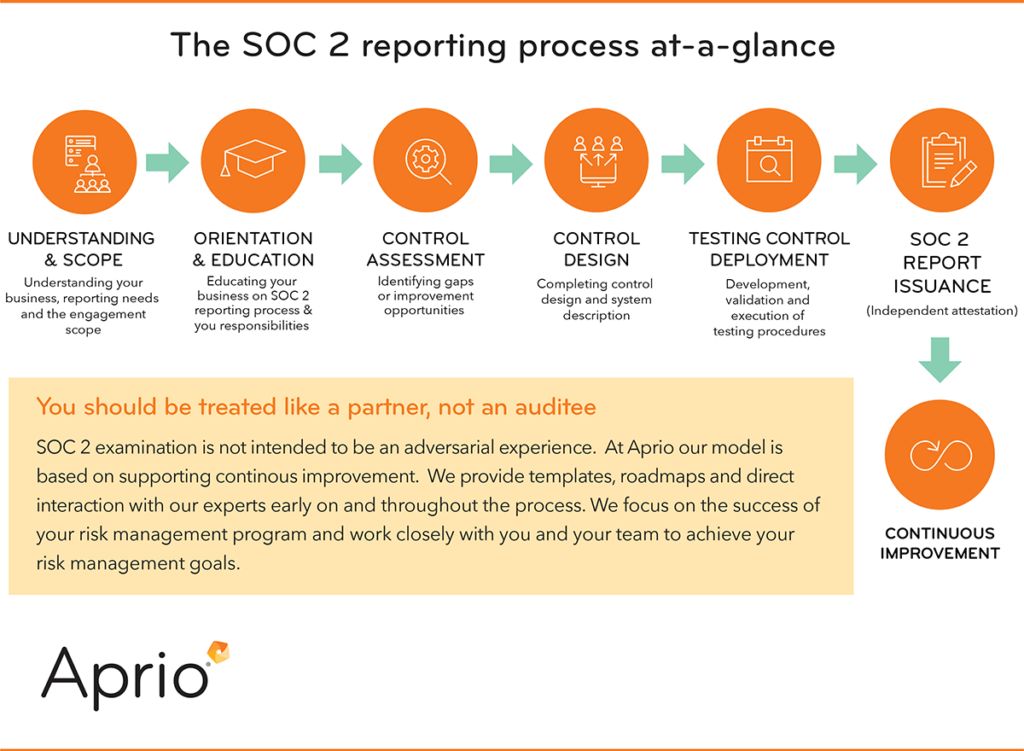
You should be treated like a partner, not an auditee.
A good SOC 2 report requires a team with audit and technical skills, a thorough understanding of the reporting standards, and deep security expertise. Your SOC 2 reporting team should be well-rounded and view themselves as strategic business partners rather than auditing and report-generating tacticians.
A sub-par SOC 2 report poses an actual risk to you, your partners and your customers.
As a client, you should expect constant feedback on matters that affect your risk profile and advice on how best to manage risk. SOC 2 examination is not intended to be an adversarial experience. Successful audit partners add value to their clients’ risk management program, while also adhering to assurance reporting protocols.
If you’re serious about risk management, look for a provider that is competent and confident enough to provide candid guidance throughout the process. Organizations going after their first SOC 2 report often start by identifying and fixing gaps before the SOC examination period begins. A good SOC 2 provider will use the SOC 2 framework to help you prepare for a successful examination and a relevant, useful report.
For example, at Aprio we treat our clients like partners, not “auditees”. We provide templates, roadmaps and direct interaction with our experts early on and throughout the process. We focus on the success of your risk management program and work closely with you and your team to achieve your risk management goals.
Armed with a relevant, useable SOC 2 report, you’ll have much more than a seal of approval to show for your investment. You’ll have a solid framework upon which to build and maintain a dynamic, effective information security program — as SOC 2 was intended.
If you are interested in engaging an information assurance partner that will help you make SOC 2 reporting a cornerstone of your ongoing information risk management program, contact Dan Schroeder, CPA, CISA, CRISC, CIOO/IT, PCI-QSA, Partner-in-Charge, Aprio Information Assurance Services.
Stay informed with Aprio.
Get industry news and leading insights delivered straight to your inbox.

