PCI DSS v4.0: Navigating Changes and the Implementation Timeline
October 9, 2023
At a glance
- Main takeaway: PCI DSS v4.0 is here and signals a substantial evolution in safeguarding payment card data. Now is the time for your company to start preparing to make the shift.
- Impact on your business: While the PCI Security Standards Council has provided a long runway to become PCI DSS v4.0 compliant, there are 66 new requirements, 15 of which must be immediately implemented upon adoption.
- Next steps: Aprio’s Information Assurance Services team is leading the way with PCI DSS v4.0 implementation. Let us help you take the next step in becoming PCI DSS v4.0 ready.
Are you ready to learn more? Schedule a conversation with our team.
The full story:
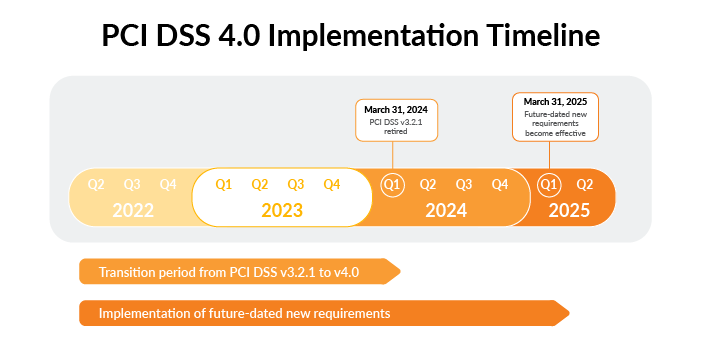
As the digital landscape evolves, so does the quest to safeguard sensitive payment data. On March 31, 2024, the Payment Card Industry Data Security Standard (PCI DSS) v3.2.1 will officially retire, and the new iteration of PCI DSS v4.0 becomes mandatory. This revamped version ushers in a series of updates that reshape the compliance landscape. In this article, we breakdown the key elements and pivotal dates that businesses need to be aware of.
Effective Dates and Transition Period
The transition from PCI DSS v3.2.1 to the freshly minted v4.0 introduces a host of changes in both compliance reporting and new security requirements. The PCI Security Standards Council (SSC) has constructed a long runway for the shift, and Aprio has been busy over the past year onboarding 100% of our clients onto the PCI v4.0 standard ahead of the March 31, 2024, deadline. This date marks the formal retirement of v3.2.1 and the official inauguration of v4.0 as the singular standard.
Deciphering Immediate vs Future Dated Requirements
Effective immediately upon adoption of PCI DSS v4.0, 15 of the 66 new requirements become immediately applicable, though 11 of these may be addressed in a single effort across requirements 1 to 11 of PCI DSS’s high level family of requirements.
The remaining 51 requirements must be implemented by March 31, 2025, based on their applicability to the entity based on scope and the entity’s classification as a Third-Party Service Provider (TSPS) or Merchant.
PCI requirements effective immediately:
| PCI Req # | Requirement | Applicability |
| 1-11: X.1.2 | Roles and responsibilities for performing activities (in requirements 1-11) are documented, assigned and understood. | All Entities |
| 6.3.3 | Both critical and high security patches must be installed within one month of release. (Previously this requirement only applied to critical security patches) | All Entities |
| 12.5.2 | Document / confirm PCI scope at least every 12 months and upon significant changes. | All Entities |
| 12.9.2 | TPSPs must support customers’ requests to provide PCI DSS compliance status and information about PCI DSS requirements that are the responsibility of the TPSP. | Third-Party Service Providers |
Exploring What is New in PCI DSS v4.0
PCI DSS v4.0 introduces a grand total of 66 fresh requirements. However, it’s crucial to note that only 15 of these 66 take immediate effect under v4.0, while the remaining 51 are considered best practices until they become mandatory on March 31, 2025.
Get our free PCI 4.0 New Requirements Implementation Fieldguide, which provides a complete breakdown of all 64 new requirements, and detailed guidance on how to implement and demonstrate compliance with each.
Beyond the introduction of new requirements, the essence of v4.0 lies in a triad of changes classified as follows:
PCI DSS v4.0: Evolving Requirements
Comprising of about 80 changes, these adjustments keep the standard abreast of emerging threats, technologies and shifts in the payment domain. This category involves adding, removing, and modifying requirements and testing protocols.
Some examples:
- Requirement 3.2.1 introduces a new requirement to address sensitive authentication data (SAD) stored prior to completion of authorization through implementation of data retention and disposal policies, procedures and processes.
- Requirement 8.3.9 introduces an option to implement a solution that allows the entity to determine access to resources automatically by dynamically analyzing the security posture of accounts, instead of requiring mandatory changing of passwords/passphrases at least once every 90 days.
PCI DSS v4.0: Clarification or Guidance
Over a hundred edits fall into this category, designed to enhance comprehension, and offer nuanced insights. Examples include refining terminologies, explaining situations and offering additional guidance.
Some examples:
- Requirement 6.2.1 replaced references to “internal and external” with “bespoke and custom” software. This was done to clarify that this requirement applies to software developed for or by the entity for the entity’s own use and does not apply to third-party software.
- Requirement 9.5.1 clarified that the focus of the requirement is on “Point-of-interaction (POI) devices that capture payment card data via direct physical interaction with the payment card form actor.” PCI also clarified that this requirement applies to deployed POI devices used in card-present transactions.
PCI DSS v4.0: Structure or Format
Roughly 53 edits made in PCI DSS v4.0 were classified as changes introduced to reconfigure content for better alignment. This entails merging, separating and renumbering requirements, ensuring precision in their application. These changes have applied throughout the standard.
A complete list of these changes has been published by the PCI SSC and can be found in the document library on the Security Council website. You can also download a copy of the document directly here.
Introduction of the PCI DSS Customized Approach
A new facet in v4.0 of PCI DSS is the Customized Approach. The Customized Approach gives additional flexibility to organizations using different security technologies that meet the intent of PCI DSS requirements, while not being able to comply with the traditional, defined approach to meeting a requirement.
The Customized Approach allows for implementation of tailored methods and controls for meeting a PCI DSS requirement based on addressing the risk objective of a requirement. It empowers organizations to implement controls most suited to their environment, with assessors crafting testing procedures tailored to the specific solutions in place.

Supporting the Customized Approach
To facilitate this novel approach, v4.0 introduces new requirements and tools. Notably:
- Requirement 12.3.2 mandates targeted risk analysis for each PCI DSS requirement fulfilled via the Customized Approach.
- Appendix D provides insights and instructions for navigating the Customized Approach.
- Appendix E furnishes templates for the Customized Approach, such as the Controls Matrix and Risk Analysis.
While it may be tempting to use this tool, Aprio is recommending that our clients employ it sparingly due to the additional compliance burden it places on the organization. To date, its usage has been limited to emerging technologies and bleeding edge scenarios. The PCI Security Standards Council has published an informative post helping entities determine if the customized approach is right for them.
PCI DSS v4.0 is Here. Are You Ready?
PCI DSS v4.0 signals a substantial evolution in safeguarding payment card data. As businesses adapt to these changes, the overarching objective remains unaltered — securing the financial transactions that underpin our digital age.
Aprio is leading the way with the implementation of PCI DSS v4.0. Our Information Assurance Services team has developed plans for 100% of our clients and are proud to state that our entire client base is PCI DSS v4.0 ready.
If you are ready to take the next step in demystifying PCI DSS v4.0, request a copy of our PCI DSS v4.0 Field Guide and PCI By the Numbers guides to help you fast track implementation of your PCI program!
Related Resources
Navigating the Impact of PCI DSS v4.0: The Top 9 New Requirements Service Providers Need to Be Aware of
PCI DSS v4.0 New MFA Requirements
About Aprio’s Information Assurance Services
Recent Articles
About the Author
Shane Peden
Shane Peden has more than 10 years of experience in information security services. He works with CEOs, CFOs and CIOs, concentrating on high-growth technology companies and startups operating in a variety of industries. Shane has extensive experience helping clients successfully scope, plan, implement and obtain their information security certifications, such as PCI, HITRUST, ISO 27001 and SOC 2.
Stay informed with Aprio.
Get industry news and leading insights delivered straight to your inbox.

