NIST CSF 2.0 – Critical Updates and Need to Know Information
April 2, 2024
At a glance:
- The main takeaway: NIST has completed the first significant revision to the CSF. The core of the CSF remains the same, but the update brings some major changes and enhancements aimed at making the framework more efficient and effective.
- The impact on your business: NIST CSF 2.0 has been expanded to provide a valuable framework for reducing cybersecurity risks for organizations of any size in any industry.
- Next steps: Consider what the new framework means for your business, then reach out to Aprio’s Cybersecurity and Compliance specialists for help reducing your organization’s cybersecurity risk.
Schedule a consultation with Aprio’s Technology Advisory Services team today.
The full story:
The National Institute of Standards and Technology (NIST) has completed the first significant revision to the Cybersecurity Framework (CSF) since the framework was established in 2014. The revision offers several enhancements to NIST CSF, but it’s important to note that most of the framework core has stayed the same. This revision is the result of a long process of consultations and public feedback aimed at making the framework more efficient.
Here are the main things you should know about the changes:
NIST CSF 2.0 has a new Govern Function
One of the most important changes to NIST CSF is that the framework now has a new Govern Function to highlight the outcomes of cybersecurity risk management governance. The Govern Function is now at the core of the other pillars, as it guides how an organization will carry out the other five Functions. The CSF’s governance component stresses that cybersecurity is a major type of enterprise risk that senior leaders should weigh along with others such as finance and reputation.
With the addition of the new Govern Function, the framework is now based on six key functions:
- Govern: establish and monitor your company’s cybersecurity risk management strategy, expectations and policy.
- Identify: determine the current cybersecurity risk to the business.
- Protect: support your ability to use safeguards to prevent or reduce cybersecurity risks.
- Detect: find and analyze possible cybersecurity attacks and compromises.
- Respond: take action regarding a detected cybersecurity incident.
- Recover: restore assets and operations impacted by a cybersecurity incident.
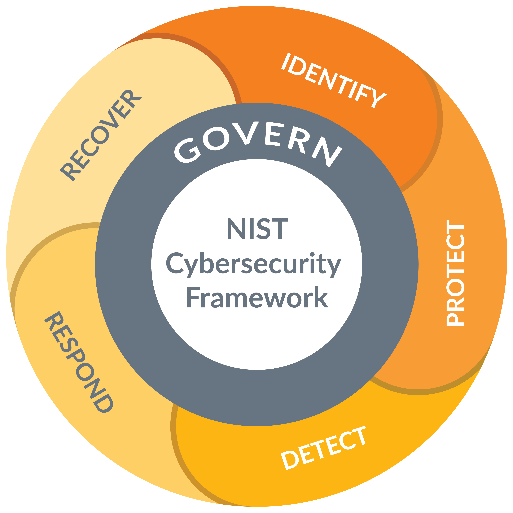
Image Source: https://www.nist.gov/news-events/news/2023/08/nist-drafts-major-update-its-widely-used-cybersecurity-framework
NIST CSF 2.0 has been expanded to apply to any organization, not only critical infrastructure
In the past, NIST CSF focused primarily on critical infrastructure. The NIST CSF 2.0 framework has been modified to suit any sector and cover a variety of organizations with different sizes and levels of cybersecurity program development whether they are in government, industry or academia. By expanding the scope of NIST CSF 2.0, the framework becomes useful for all organizations, no matter their sector, type or size. CSF 2.0 also includes CSF tiers in an appendix, which shows the different stages of how well an organization manages cybersecurity risks.
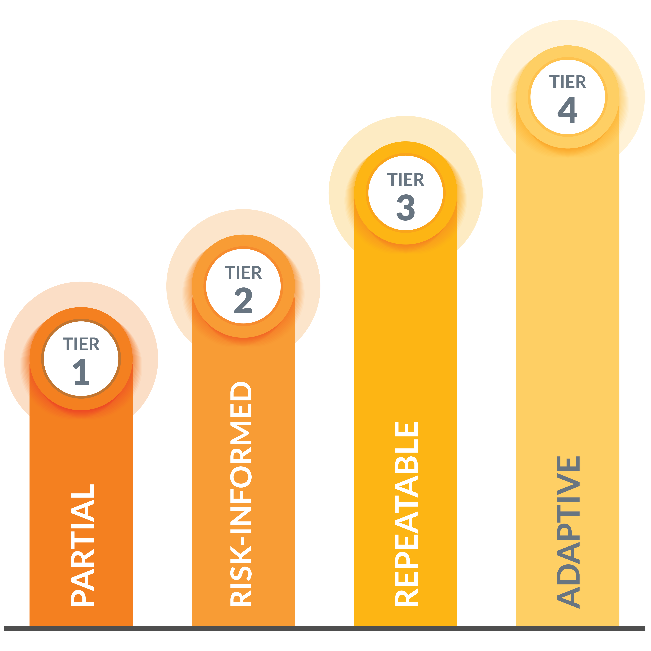
These four CSF Tiers are:
- Tier 1: Partial
- Organizations at this tier have some cybersecurity practices in place, but they are not systematic or well-coordinated.
- There is no formal risk management program, and cybersecurity decisions are made on an ad-hoc basis.
- Tier 2: Risk Informed
- Organizations at this tier have a more formal approach to cybersecurity, but their practices are still evolving.
- They have begun to identify and assess their cybersecurity risks, and they are taking steps to mitigate those risks. However, their risk management program is not yet fully mature.
- Tier 3: Repeatable
- Organizations at this tier have a well-defined and repeatable approach to cybersecurity risk management.
- They have a formal risk management program in place, and they are regularly assessing their cybersecurity risks and taking steps to mitigate those risks. Their cybersecurity controls are implemented in a consistent manner.
- Tier 4: Adaptive
- Organizations at this tier are constantly improving their cybersecurity posture.
- They have a mature risk management program in place, and they are able to quickly adapt to new threats and vulnerabilities. Their cybersecurity controls are continuously monitored and updated.
NIST has published a host of new tools for CSF 2.0
NIST has developed a set of resources to assist every organization in meeting their cybersecurity objectives, with extra focus on governance and supply chains. These resources are intended to offer different users with customized entry points into the CSF and make the framework simpler to use.
NIST CSF Reference Tool: With NIST CSF’s new reference tool, organizations can use the CSF more easily, as they can view, search and export information and specifics from the CSF’s core guidance in formats that are readable by humans and machines.
NIST CSF Searchable Catalog: The CSF 2.0 provides a searchable catalog of useful references that enables organizations to compare the CSF’s recommendations to more than 50 other cybersecurity documents, such as NIST 800-53.
NIST CSF Community Profiles: NIST has created new community profiles to help organizations learn how their peers are applying the framework. NIST CSF is a versatile framework that can be used for various purposes, and these community profiles show how different sectors adjust the framework’s terminology to suit their specific needs.
NIST CSF Implementation Examples: Many organizations with different needs rely on NIST CSF, and because of that there has been confusion over what NIST CSF implementation looks like across different organizations. NIST has published implementation examples which offer detailed information like connections and mappings to specific cybersecurity guidance from NIST and other organizations to help with implementation guidance. These practical steps help you comprehend the outcomes of the subcategories and address many of your questions on how to begin.
Quick Start Guides: NIST has developed a series of targeted guides, designed for small businesses, enterprise risk managers, and organizations seeking to secure their supply chains.
How Aprio is helping entities implementing NIST CSF 2.0
Aprio’s compliance as a service security team assists organizations in applying the NIST CSF 2.0 risk management framework, facilitates continuous control assessment efforts, and enhances the security of an organization’s information systems.
Many of our clients implement the CSF as a management framework to drive their security program. We can help you do this through:
- Implementing a program and platform to assist you with gaining a complete view of all of your compliance efforts
- Using NIST CSF 2.0 requirements to support demonstrating compliance with other cybersecurity and data privacy standards
- Tracking your progress towards compliance, assign tasks and prioritize work streams
- Supporting enterprise information risk management, security and IT budgeting, and executive reporting
If you’re currently using NIST CSF 1.1 and looking for support to help you upgrade to 2.0 when the time is right, we have also developed a plan to streamline this process.
Schedule a consultation with Aprio’s Cybersecurity and Advisory Services team today for help upgrading to NIST CSF 2.0.
Related Resources:
Security & Compliance at Sandata: From Headache to Head Start
Migrating to the Cloud: Security Should Be Your Priority, Not an Afterthought
Tech Over Troubled Waters: Six Questions Facing the Tech Industry Right Now
Recent Articles
About the Author
Shane Peden
Shane Peden has more than 10 years of experience in information security services assisting high-growth technology companies and startups, operating in a variety of industries. He works closely with CEOs, CFOs and CIOs who need help demonstrating their information security maturity to customers.
Stay informed with Aprio.
Get industry news and leading insights delivered straight to your inbox.

